Perspectives
Academic perspectiveedit
In an academic context, the Association for Computing Machinery defines IT as "undergraduate degree programs that prepare students to meet the computer technology needs of business, government, healthcare, schools, and other kinds of organizations .... IT specialists assume responsibility for selecting hardware and software products appropriate for an organization, integrating those products with organizational needs and infrastructure, and installing, customizing, and maintaining those applications for the organization’s computer users."
Commercial and employment perspectiveedit
Companies in the information technology field are often discussed as a group as the "tech sector" or the "tech industry".
Many companies now have IT departments for managing the computers, networks, and other technical areas of their businesses.
In a business context, the Information Technology Association of America has defined information technology as "the study, design, development, application, implementation, support or management of computer-based information systems".page needed The responsibilities of those working in the field include network administration, software development and installation, and the planning and management of an organization's technology life cycle, by which hardware and software are maintained, upgraded and replaced.
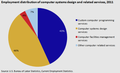
U.S. Employment distribution of computer systems design and related services, 2011

U.S. Employment in the computer systems and design related services industry, in thousands, 1990-2011

U.S. Occupational growth and wages in computer systems design and related services, 2010-2020
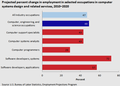
U.S. projected percent change in employment in selected occupations in computer systems design and related services, 2010-2020

U.S. projected average annual percent change in output and employment in selected industries, 2010-2020
Ethical perspectivesedit
The field of information ethics was established by mathematician Norbert Wiener in the 1940s.:9 Some of the ethical issues associated with the use of information technology include::20–21
- Breaches of copyright by those downloading files stored without the permission of the copyright holders
- Employers monitoring their employees' emails and other Internet usage
- Unsolicited emails
- Hackers accessing online databases
- Web sites installing cookies or spyware to monitor a user's online activities




Comments
Post a Comment